Enhance Your Information Defense With Trusted Cloud Storage Space Provider
Trusted cloud storage space solutions use a safe sanctuary for important details, but what establishes these carriers apart in terms of information security? Stay tuned to uncover the essential components that might fortify your information protection strategy and boost your safety posture in the ever-evolving world of cloud storage solutions.
Importance of Information Safety And Security
Ensuring robust data protection procedures is paramount in today's electronic landscape to safeguard delicate info from unapproved gain access to or violations. With the increasing reliance on electronic platforms for saving and accessing data, the threat of cyber risks has actually likewise risen. Data violations can result in severe effects such as financial loss, reputational damages, and legal implications for people and businesses alike. To alleviate these threats, organizations have to prioritize data protection by applying strong security protocols, gain access to controls, and normal safety audits.
Advantages of Trusted Suppliers
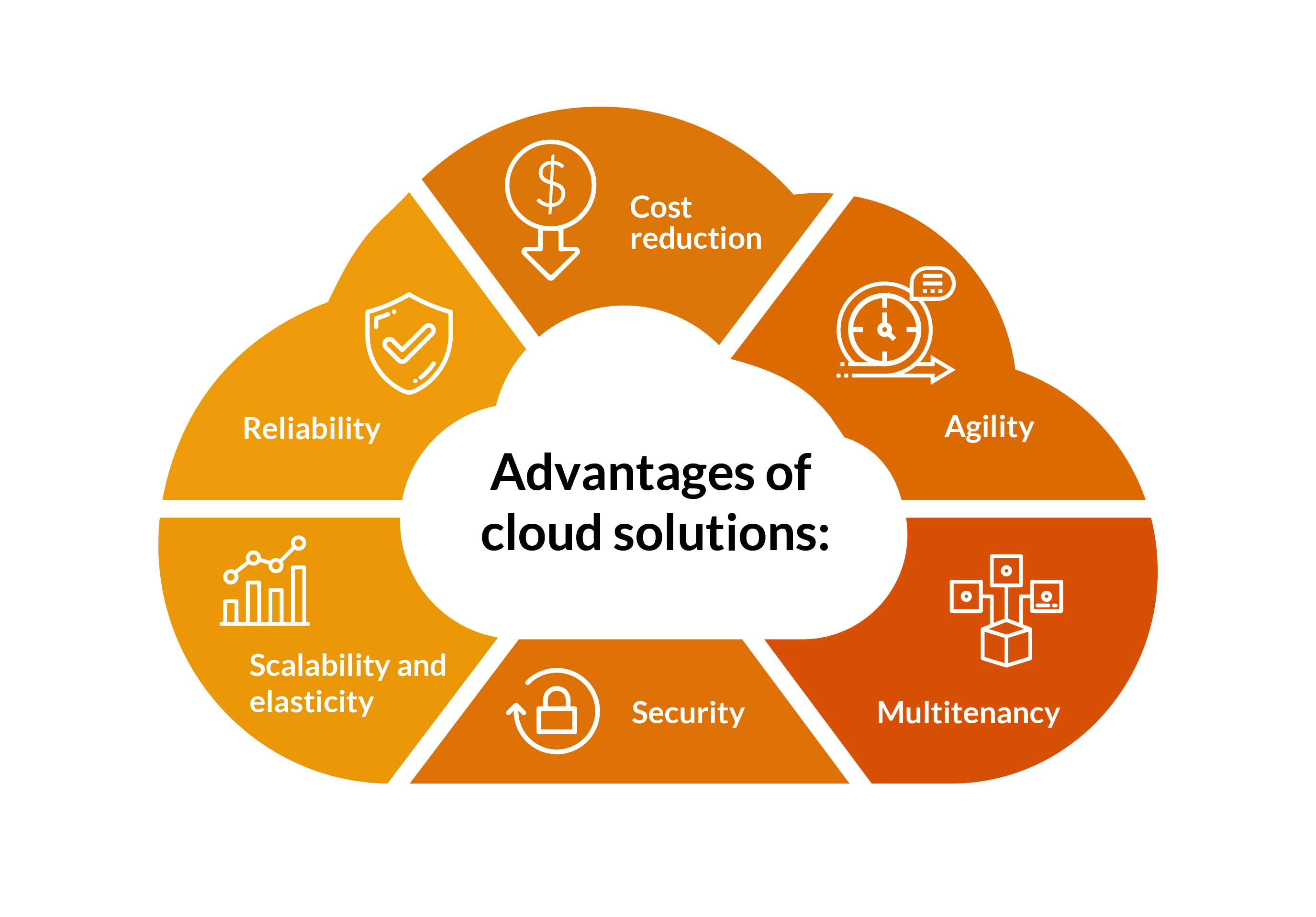
Partnering with respectable cloud storage space carriers offers a range of benefits for organizations seeking robust information protection solutions. Trusted service providers provide improved security measures, such as security methods, multi-factor verification, and normal protection audits, to guarantee the confidentiality and integrity of stored information. By handing over sensitive info to trustworthy cloud solutions, companies can gain from advanced cybersecurity modern technologies and experienced upkeep, minimizing the risk of data breaches and unapproved gain access to.
Additionally, trusted cloud storage suppliers commonly ensure high availability and integrity through redundant storage space systems and data backup procedures. This makes certain that organizations can access their data whenever needed, without experiencing downtime or disturbances. Additionally, reputable carriers supply scalable storage options, enabling organizations to adjust their storage space capacity according to their advancing requirements without compromising data safety.
In addition, partnering with trusted cloud storage space carriers can lead to price savings for organizations, as they remove the requirement for buying costly framework and maintenance. By leveraging the know-how and resources of well-known cloud services, organizations can concentrate on their core procedures while ensuring the security and availability of their information.
Attributes to Search For
When assessing cloud storage services, organizations should prioritize vital attributes that straighten with their data security requirements and operational demands. Additionally, robust accessibility controls are crucial for restricting who can see, edit, or delete information within the cloud storage environment.
An additional essential function is information redundancy and backup capabilities. Cloud storage space solutions that offer automated backups and redundant storage space make sure that information continues to be easily accessible even in the occasion of hardware failings or disasters. Versioning capacities are likewise advantageous, enabling companies to restore previous variations of data in case of find unintended deletions or undesirable modifications. Trustworthy uptime guarantees and service level contracts (SLAs) should be thought about to ensure regular access to information whenever required. By prioritizing these functions, companies can enhance their information defense techniques when useful source choosing a cloud storage space solution.

Ideal Practices for Data Defense
To reinforce information protection procedures in cloud storage space services, companies have to comply with finest techniques that safeguard sensitive information and ensure functional connection. One crucial technique is implementing strong encryption techniques to secure information both in transit and at rest. File encryption assists protect against unauthorized access to private information, including an added layer of protection. Frequently upgrading protection procedures and spots is an additional essential practice. With cyber risks continuously advancing, keeping systems up-to-date helps address vulnerabilities and fortify defenses against potential breaches.
 Additionally, companies should enforce strict gain access to controls to limit the number of people that can watch or modify sensitive information. By implementing role-based access and multi-factor authentication, business can minimize the danger of unauthorized gain access to. On a regular basis supporting information and screening calamity healing strategies are likewise essential practices. In case of information loss or a security incident, having dependable backups makes certain that info can be brought back quickly, reducing downtime and operational disturbances. By complying with these best techniques, organizations can enhance their information security techniques and reduce potential threats related to cloud storage services.
Additionally, companies should enforce strict gain access to controls to limit the number of people that can watch or modify sensitive information. By implementing role-based access and multi-factor authentication, business can minimize the danger of unauthorized gain access to. On a regular basis supporting information and screening calamity healing strategies are likewise essential practices. In case of information loss or a security incident, having dependable backups makes certain that info can be brought back quickly, reducing downtime and operational disturbances. By complying with these best techniques, organizations can enhance their information security techniques and reduce potential threats related to cloud storage services. Making Certain Compliance and Regulations
Adherence to conformity demands and laws is vital for organizations using cloud storage solutions to protect information stability and personal privacy. When handing over sensitive information to a third-party cloud service provider, organizations have to ensure that the picked service adhere to industry-specific policies such as GDPR, HIPAA, or PCI DSS, depending on the nature of the information being stored. Carrying out complete due diligence to confirm the cloud provider's adherence to these requirements is crucial in preserving legal and regulative compliance.
Moreover, companies need to establish clear plans and treatments for data dealing with and access control to meet regulatory needs. Inevitably, making certain conformity and guidelines within cloud storage practices is basic in promoting data safety and personal privacy requirements.
Verdict
In conclusion, prioritizing data safety via trusted cloud storage solutions is vital for guarding sensitive info and mitigating threats in the electronic landscape. Trusted cloud storage services use scalability, high availability, and expense financial savings for companies seeking reputable data defense services.
 Furthermore, trusted cloud storage providers typically assure high availability and dependability continue reading this with redundant storage space systems and information backup processes. In addition, credible carriers use scalable storage space options, enabling companies to adjust their storage capacity according to their progressing demands without compromising data safety.
Furthermore, trusted cloud storage providers typically assure high availability and dependability continue reading this with redundant storage space systems and information backup processes. In addition, credible carriers use scalable storage space options, enabling companies to adjust their storage capacity according to their progressing demands without compromising data safety.Cloud storage space services that use automatic backups and redundant storage make certain that data stays obtainable also in the event of hardware failings or disasters.To reinforce information security measures in cloud storage solutions, companies must adhere to best methods that secure delicate details and make certain operational connection. By adhering to these ideal techniques, organizations can enhance their data protection strategies and reduce prospective risks linked with cloud storage solutions.